How Does the Dbms Decide Which Hashing Algorithm to Use
Generally these hash codes are used to generate an index at which the value is stored. DBMS_SQLHASH provides support for several industry standard hashing.
Hashing Function In C Types Of Collision Resolution Techniques
Hashing is generating a value or values from a string of text using a mathematical function.

. 3 The hash function uniformly distributes the data across the entire set of possible hash values. When a hash function is used to provide message authentication the hash function value is referred to as. The hashing algorithm evenly distributes rows among partitions giving partitions approximately the same size.
The Secure Hash Algorithm standard considers it as the second one version. A good hash algorithm should be complex enough such that it does not produce the same hash value from two different inputs. Cryptocurrency algorithms are a set of specific cryptographic mechanisms and rules that encrypt a digital currency.
It works the same way as the DBMS_CRYPTOHASH function except only someone with the key can verify the hash value. Generally the Hash function is at the heart of a hashing algorithm. Hash values are like data fingerprints and are used to ensure data integrity.
Most of the time the hash function uses the primary key to generate the address of the data block. Use keyed hashing algorithms to protect the hash from being modified. Nested Loops Indexed Nested Loops Sort-Merge Hash Join Reserves Sailors sidsid bid100 rating 5 sname Simple Nested Loops On-the-fly On-the-fly.
Due to these issues the MD5 got out of common use. For data verification you can allow others to view a hash but you must protect it from being modified. A hash is usually a hexadecimal string of several characters.
The HASH function included with DBMS_CRYPTO is a one-way hash function that you can use to generate a hash value from either RAW or LOB data. 160-bit outputs is the featureof SHA-1 hashing algorithm. 5- join characters and add 1 to the end.
One of the common cryptographic hash algorithms is SHA 256. The main difference in MACs and digital signatures is that in digital signatures the hash value of the message is encrypted with a users public key. It is also one of the foremost algorithms which started to update MD5.
The updates were done after finding the. So a computing the hash of large number of files will not be a problem. 2 The hash function uses all the input data.
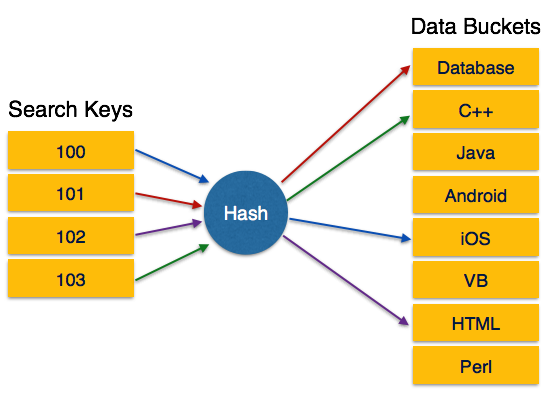
Selection either scan all tuples or use index Projection expensive only if duplicates eliminated requires sorting or hashing Join several algorithms. If I want to divide representations of numbers into buckets so that representations of the same number are in the buckets I can choose bucket by hash code. 1 The hash value is fully determined by the data being hashed.
Use hashing algorithms to verify integrity and store passwords. In this a hash function can choose any of the column value to generate the address. The DBMS_SQLHASH package can check data integrity by making use of hash algorithms.
You do it by computing hash of that file using a Cryptographic hash algorithm. In this case we will choose the word CRYPTO. A formula generates the hash which helps to protect the security of the transmission against tampering.
Hash partitioning is the ideal method for distributing data evenly across devices. So how does a hashing algorithm work in this case a look at SHA1. This so-called hash code or simply hash can then be used as a way to narrow down our search when looking for the item in the map.
What is the size of the RSA signature hash after the MD5 and SHA-1 processing. 2- Then choose a word to hash. The hash thus computed has a maximum size of 32 bytes.
It provides an interface to generate the hash value of the result set returned by a SQL query. But to get the hash-value of a pre-defined length first its required to divide the input data into the blocks of fixed-sized because a hash function takes data in a fixed length. You save these hashes on your local machine.
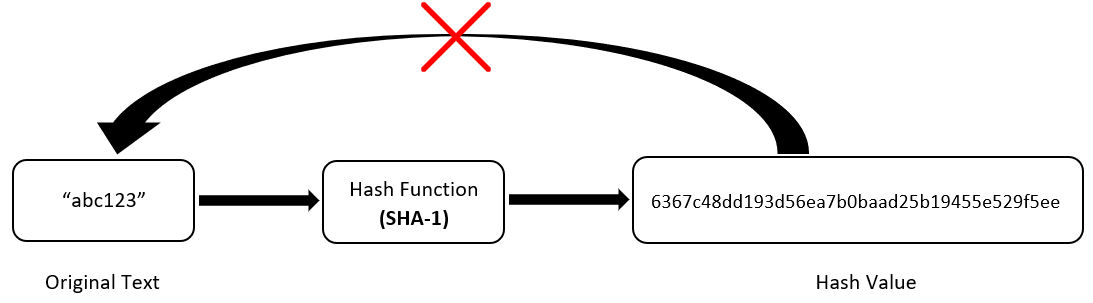
Hashing is also a unidirectional process so you can never work backwards to get back the original data. Hashing Techniques In DBMS. The MAC function is also a one-way hash function but with the addition of a secret key.
Hashing produces a hash code. It does not always produce a perfect result but its imperfections can be mitigated for by an algorithm designer who is aware of them. It is an aggressively flexible method in which the hash function also experiences dynamic changes.
There are four main characteristics of a good hash function. What Does Hashing Algorithm Means. Each letter has a number assigned to it.
Miners using special equipment decrypt the algorithm of a particular cryptocurrency. A hash function is a simple mathematical function to any complex mathematical function. It hosts well written and well explained computer science and engineering articles quizzes and practicecompetitive programmingcompany interview Questions on subjects database management systems operating systems information retrieval natural language processing computer networks.
Hashing is heuristic ie. If it does this is known as a hash collision. Hashing is one way to enable security during the process of message transmission when the message is intended for a particular recipient only.
Although they have been designed to be a one-way function impossible to invert a lot of hashing algorithms have been compromised in time. Typically 1 complete disc block which in turn can. A portal for computer science studetns.
Main features of Extendible Hashing. Also these blocks are known as data blocks which are shown in the below-mentioned image. Hash partitioning is also an easy-to-use alternative to range partitioning especially when the data to be partitioned is not historical or has no.
The main features in this hashing technique are. Overview of the DBMS_SQLHASH Package. In the above formulas k mod m indicates the remainder when k is divided by m.
3- Convert the word to ASCII American Standard Code for Information Interchange. A hashing algorithm is a cryptographic hash function that maps data of random size to a hash of a specific size. The SHA-zero being the first.
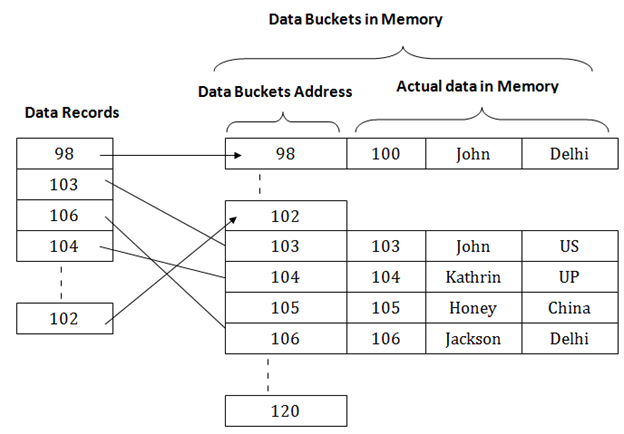
This process consists of finding a hash. Hash file stores data in bucket format a bucket is nothing but a unit of storage. We can even consider the primary key itself as the address of the data block.
As soon as the correct hash is found a new block is generated in the. Division method- A hash function which uses division method is represented as. For password authentication keep the hashes secret to prevent brute-force attacks.
Hashing is an effective technique to calculate the direct location of the data record on the disk using a function key without using a sequential index structure as a result data retrieval time decreases. Extendible Hashing Dynamic approach to DBMS Extendible Hashing is a dynamic hashing method wherein directories and buckets are used to hash data. Which is greater than total no.
K signifies a hash key and m is chosen to be a prime no. Hashing means using some function or algorithm to map object data to some representative integer value.

Types Of Data Abstraction In Dbms Physical Logical View Data Link Layer Dbms Data Structures

File Organization In Dbms Set 2 Geeksforgeeks

Cryptographic Hash Function In Java Geeksforgeeks

Midpoint Ellipse Drawing Algorithm In Computer Graphics In Python In 2022 Algorithm Midpoint Ellipse
Hash Join Algorithm Vlad Mihalcea
Hash Functions Definition Usage And Examples Ionos
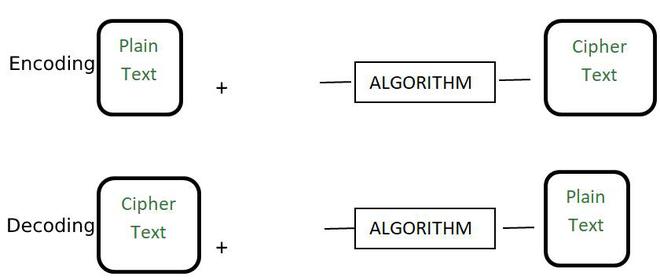
Difference Between Hashing And Encryption Geeksforgeeks
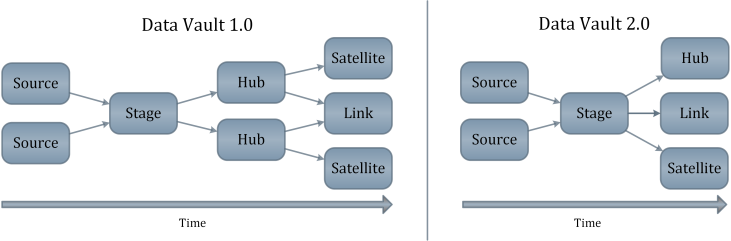
Hash Keys In The Data Vault Experts In Consulting And Training
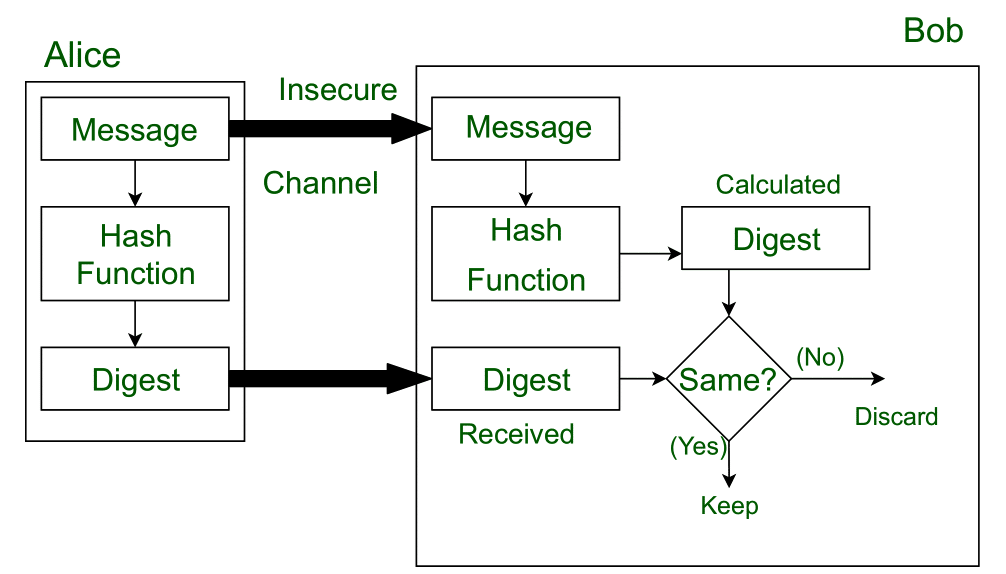
Message Digest In Information Security Geeksforgeeks
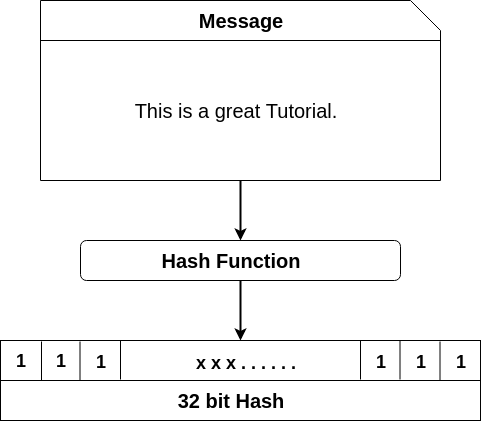
Blockchain Hash Functions Javatpoint
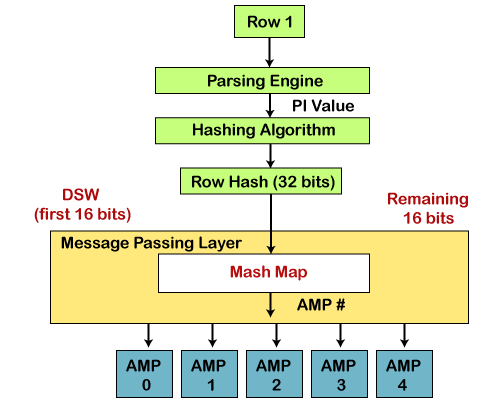
Teradata Hashing Algorithm Javatpoint

Create Light Weight Object In Python And Named Tuple Examples In 2022 Object Oriented Programming Algorithm Names
Introduction To Hashing What Is A Hash Function By Isuru Jayathilake Medium

Draw Line In Python Using Pil With Explanation In 2022 Python Explanation Draw
Comments
Post a Comment